 You’ve installed an SSL Certificate to secure your Plesk Panel, you’ve tested it with an SSL checker and sure enough: the ugly warning window doesn’t bother you or your customers anymore.
You’ve installed an SSL Certificate to secure your Plesk Panel, you’ve tested it with an SSL checker and sure enough: the ugly warning window doesn’t bother you or your customers anymore.
But your email client still says that the server doesn’t have a valid certificate. What gives?
The secret is this: SMTP, IMAP and POP3 use their own certificates which are not related to the ones you setup in Plesk to secure https connections. By default the mail services use auto-generated self-signed certificates.
Sadly as of Plesk 12 there is still no way to manage those in the web interface – but it’s relatively easy to fix on the command line. Let’s go through this step by step.
These instructions are for Plesk 12 on CentOS 6 and CentOS 7, using the default Courier mail service. You can also install an alternative mail service called Dovecot in Plesk 12. I’m discussing how to install Dovecot over here.
Default Certificates
We need to replace the following three files (default permissions in brackets):
- /etc/postfix/postfix_default.pem (600)
- /usr/share/imapd.pem (400)
- /usr/share/pop3d.pem (400)
Those are the culprits for SMTP, IMAP and POP3. We need to add our own private key and the certificate of a domain associated with this server and remove the default certificates.
Before we begin, make a safety copy of them like this:
mv /etc/postfix/postfix_default.pem /etc/postfix/postfix_default.old mv /usr/share/imapd.pem /usr/share/imapd.old mv /usr/share/pop3d.pem /usr/share/pop3d.old
Here we rename the original files to .old files – in case anything goes wrong, simply rename them back into .pem files.
Add your own certificate
We need the same file three times, so we’ll start by making one for the SMTP service. Create a new file like this:
vi /etc/postfix/postfix_default.pem
and paste first the private key, followed by your certificate into this file. It will look something like this:
-----BEGIN PRIVATE KEY----- MIID1TCCAr2gAwIBAgIDAjbRMA0GCSqGSIb3DQEBBQUAMEIxCzAJBgNVBAYTAlVT MRYwFAYDVQQKEw1HZW9UcnVzdCBJbmMuMRswGQYDVQQDExJHZW9UcnVzdCBHbG9i YWwgQ0EwHhcNMTAwMjE5MjI0NTA1WhcNMjAwMjE4MjI0NTA1WjA8MQswCQYDVQQG EwJVUzEXMBUGA1UEChMOR2VvVHJ1c3QsIEluYy4xFDASBgNVBAMTC1JhcGlkU1NM IENBMIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEAx3H4Vsce2cy1rfa0 l6P7oeYLUF9QqjraD/w9KSRDxhApwfxVQHLuverfn7ZB9EhLyG7+T1cSi1v6kt1e 6K3z8Buxe037z/3R5fjj3Of1c3/fAUnPjFbBvTfjW761T4uL8NpPx+PdVUdp3/Jb ewdPPeWsIcHIHXro5/YPoar1b96oZU8QiZwD84l6pV4BcjPtqelaHnnzh8jfyMX8 N8iamte4dsywPuf95lTq319SQXhZV63xEtZ/vNWfcNMFbPqjfWdY3SZiHTGSDHl5 HI7PynvBZq+odEj7joLCniyZXHstXZu8W1eefDp6E63yoxhbK1kPzVw662gzxigd gtFQiwIDAQABo4HZMIHWMA4GA1UdDwEB/wQEAwIBBjAdBgNVHQ4EFgQUa2k9ahhC St2PAmU5/TUkhniRFjAwHwYDVR0jBBgwFoAUwHqYaI2J+6sFZAwRfap9ZbjKzE4w EgYDVR0TAQH/BAgwBgEB/wIBADA6BgNVHR8EMzAxMC+gLaArhilodHRwOi8vY3Js Lmdlb3RydXN0LmNvbS9jcmxzL2d0Z2xvYmFsLmNybDA0BggrBgEFBQcBAQQoMCYw JAYIKwYBBQUHMAGGGGh0dHA6Ly9vY3NwLmdlb3RydXN0LmNvbTANBgkqhkiG9w0B AQUFAAOCAQEAq7y8Cl0YlOPBscOoTFXWvrSY8e48HM3P8yQkXJYDJ1j8Nq6iL4/x /torAsMzvcjdSCIrYA+lAxD9d/jQ7ZZnT/3qRyBwVNypDFV+4ZYlitm12ldKvo2O SUNjpWxOJ4cl61tt/qJ/OCjgNqutOaWlYsS3XFgsql0BYKZiZ6PAx2Ij9OdsRu61 04BqIhPSLT90T+qvjF+0OJzbrs6vhB6m9jRRWXnT43XcvNfzc9+S7NIgWW+c+5X4 knYYCnwPLKbK3opie9jzzl9ovY8+wXS7FXI6FoOpC+ZNmZzYV+yoAVHHb1c0XqtK LEL2TxyJeN4mTvVvk0wVaydWTQBUbHq3tw== -----END PRIVATE KEY----- -----BEGIN CERTIFICATE----- MIIDfTCCAuagAwIBAgIDErvmMA0GCSqGSIb3DQEBBQUAME4xCzAJBgNVBAYTAlVT MRAwDgYDVQQKEwdFcXVpZmF4MS0wKwYDVQQLEyRFcXVpZmF4IFNlY3VyZSBDZXJ0 aWZpY2F0ZSBBdXRob3JpdHkwHhcNMDIwNTIxMDQwMDAwWhcNMTgwODIxMDQwMDAw WjBCMQswCQYDVQQGEwJVUzEWMBQGA1UEChMNR2VvVHJ1c3QgSW5jLjEbMBkGA1UE AxMSR2VvVHJ1c3QgR2xvYmFsIENBMIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIB CgKCAQEA2swYYzD99BcjGlZ+W988bDjkcbd4kdS8odhM+KhDtgPpTSEHCIjaWC9m OSm9BXiLnTjoBbdqfnGk5sRgprDvgOSJKA+eJdbtg/OtppHHmMlCGDUUna2YRpIu T8rxh0PBFpVXLVDviS2Aelet8u5fa9IAjbkU+BQVNdnARqN7csiRv8lVK83Qlz6c JmTM386DGXHKTubU1XupGc1V3sjs0l44U+VcT4wt/lAjNvxm5suOpDkZALeVAjmR Cw7+OC7RHQWa9k0+bw8HHa8sHo9gOeL6NlMTOdReJivbPagUvTLrGAMoUgRx5asz PeE4uwc2hGKceeoWMPRfwCvocWvk+QIDAQABo4HwMIHtMB8GA1UdIwQYMBaAFEjm aPkr0rKV10fYIyAQTzOYkJ/UMB0GA1UdDgQWBBTAephojYn7qwVkDBF9qn1luMrM TjAPBgNVHRMBAf8EBTADAQH/MA4GA1UdDwEB/wQEAwIBBjA6BgNVHR8EMzAxMC+g LaArhilodHRwOi8vY3JsLmdlb3RydXN0LmNvbS9jcmxzL3NlY3VyZWNhLmNybDBO BgNVHSAERzBFMEMGBFUdIAAwOzA5BggrBgEFBQcCARYtaHR0cHM6Ly93d3cuZ2Vv dHJ1c3QuY29tL3Jlc291cmNlcy9yZXBvc2l0b3J5MA0GCSqGSIb3DQEBBQUAA4GB AHbhEm5OSxYShjAGsoEIz/AIx8dxfmbuwu3UOx//8PDITtZDOLC5MH0Y0FWDomrL NhGc6Ehmo21/uBPUR/6LWlxz/K7ZGzIZOKuXNBSqltLroxwUCEm2u+WR74M26x1W b8ravHNjkOR/ez4iyz0H7V84dJzjA1BOoa+Y7mHyhD8S -----END CERTIFICATE-----
The exact same file can be used for both IMAP and POP3 so we can simply copy it to these two new locations:
cp /etc/postfix/postfix_default.pem /usr/share/imapd.pem cp /etc/postfix/postfix_default.pem /usr/share/pop3d.pem
These two files had 400 permissions by default so that only root can read them, and no one can change them. Let’s adhere to this and apply the same permissions:
chmod 400 /usr/share/imapd.pem chmod 400 /usr/share/pop3d.pem
Restart Plesk Mail Services
For the changes to take effect we’ll need to restart all Plesk mail services:
/usr/local/psa/admin/sbin/mailmng --restart-service
And that’s it! Now that pesky warning isn’t going to come up anymore when you access Plesk mail with an email client.
Adding CA Certificates
The above is enough to suppress the usual warning windows in email clients, however if you’re an avid SSL enthusiast you’ll notice that we’ve not added any CA Certificates to the above .pem files. In essence those tell a client that our certificate is valid – otherwise the client would only have our word for it.
You can add the combined CA Certificate to the end of the three .pem files in addition to the private key and your own certificate. It’s not strictly necessary, but doing this means you will pass strict SSL tests.
Thanks to Mike Yrabedra for this tip, and the test URL below!
Testing your mail services
Mike also found a wonderful service that lets you check an email address which will flag up certificate warnings and exceptions – courtesy of CheckTLS:
Simply hack in your email address and you’ll see if your certificate is installed properly. Note that to pass the test, your email address must match the domain on the certificate. For example, if your address is you@domain.com, but your certificate is for yourdomain.com then the test will fail the “Cert OK” field.
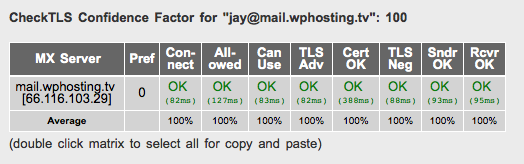
Wait – where do I find my private key and certificate?
If you’re using the same certificate for mail that you’re using to secure Plesk, simply head over to
- Tools and Settings (or the Server Tab)
- Security Settings
- SSL Certificates
- click on your certificate from the list
- scroll down to find plain text sections for your private key and certificate
Wait – where do I find that CA Certificate you speak of?
Your certificate provider will give that to you. Some providers call it “intermediate CA certificate”. They usually have several versions of the same thing. Look for a combined version. In essence it’s two plain text blocks, very similar to the ones I’ve shown you above.
For example, the RapidSSL CA certificates can be found here: https://knowledge.rapidssl.com/support/ssl-certificate-support/index?page=content&id=AR1548

All mail services are handled centrally by Plesk, not the domain. While you can of course connect to the mail server with anydomain.com, the certificate served by Plesk is always the same. If you need the functionality that a specific domain returns a specific mail certificate, I’m afraid you’ll have to use one Plesk instance for that domain. In other words, in a shared multi-domain environments, all domains must use the same mail certificates.
Hi guys. A great article but I have a question if I may. I have a VPS which has the default Parallels certificate in the postfix_default.pem file. This is used across the VPS for all domains hosted on it (under one IP address). I bought a separate SSL covering 3 domains being http://www.mydomain.co.uk, mydomain.co.uk and mail.mydomain.co.uk which is installed and working correctly but on port 443.
I’d like to use port 465 SSL in outlook and need to append/add/include the new certificate, private key and CA certificate to the existing one in the postfix default file. The question is, how do I append it as I know there is a correct format.
Do I need both Private Keys? What’s the format for adding them? I don’t want to simply overwrite the existing default certificiate as this new SSL on applies to 3 domains out of the 30 hosted.
Any help would be massively appreciated.
Kind regards
Mark.
Hi Mark,
very good question indeed – but sadly I have no idea how to add mail certificates for more than one domain. I’m not even sure it can be done in Plesk 12.5. I know that in the next version, Plesk Onyx, they’ve implemented a way to manage certificates for mail via the Plesk interface, but if that’s server-wide or per-domain I don’t know.
Your best bet is to ask one of the very knowledgable people on the Plesk forum: https://talk.plesk.com
Do let me know if you find out, it’s an interesting one! All the best,
JAY
Yust some extra info and settings on install SSL certs on Centos 7.3 / Plesk 12.5.30#60,
Using postfix (smtp) & dovecot (pop/imap).
Postfix # /etc/postfix/main.cf
smtpd_tls_cert_file = /usr/local/etc/ssl/live/cert.pem
smtpd_tls_key_file = /usr/local/etc/ssl/live/privkey.pem
smtpd_tls_CAfile = /usr/local/etc/ssl/live/ca-root-cert.pem
Dovecot # /etc/dovecot/conf.d/5-custom-ssl.conf
ssl = yes
ssl_cert = </usr/local/etc/ssl/live/cert.pem
ssl_key = </usr/local/etc/ssl/live/privkey.pem
ssl_ca = </usr/local/etc/ssl/live/ca-root-cert/AddTrustExternalCARoot.crt
ssl_ca = </usr/local/etc/ssl/live/ca-root-cert/COMODORSAAddTrustCA.crt
ssl_ca = ./live/ca-root-cert.pem
cat ./live/ca-root-cert/COMODORSADomainValidationSecureServerCA.crt >> ./live/ca-root-cert.pem
cat ./live/ca-root-cert/COMODORSAAddTrustCA.crt >> ./live/ca-root-cert.pem
chmod 444 ./live/ca-root-cert.pem
Create # ./live/chain.pem
cat ./live/privkey.pem > ./live/chain.pem
cat ./live/cert.pem >> ./live/chain.pem
Hopefully it is useful from some people, because I’ve almost no experience with ssl certs.
Goodluck, Arno